|
(Optional) This text will appear in the inbox preview, but not the email body.
 |
Information security and privacy (InfoSec) have been significant issues in the society, exacerbated by the current “big data” environment in today’s global society. By the very nature of information security, this field has been an intersection among engineering technology, economic incentive design, and human behavior. Among the various aspects of InfoSec issues, human decision making during real InfoSec situations remains one of the most critical and under-investigated issues in InfoSec. After all, it is human decision making that ultimately determines the outcomes of InfoSec planning and implementation.
Much research on information security focuses on algorithms, methods, and standards that support the three basic functions of information security: confidentiality, integrity, and availability. In addition to this basic research in computer science and mathematics, human factors experts have worked to simplify and rationalize the user interfaces of security-related systems. Likewise, management experts have analyzed business risks associated with information systems and have drafted organizational policies to cope with these risks. HPUSRA is a research project in the University of Rostock that brings behavioural study in information security for home computer users to evaluate users’ behavioural risks.
|
| The increased threats of information security brought new solutions focused on technological means, while the human factor related research has been limited.
Behavioural studies regarding information security have been emphasized in recent years. There are three main issues in the context of private useres or organizations that have attracted many scholars in this field: (1) security awareness training/education; (2) information security misuse/abuse; (3) security policy compliances. |
|
 |
| The number of home computer users is rapidly increasing. In 2008, Gartner, an American research firm published that the number of personal computers in use around the world had surpassed 1 billion; this number will double by early 2014. The large number of individual home users represents a significant point of weakness in achieving the security of the cyber infrastructure. While home users have a high chance of providing valuable information to intruders (e.g., information on emails, Internet banking, online shopping, instant messaging, and online stock trading), home users’ information security should also be a concern for organizations. This is the case, since hijacked home computers are great breading grounds for hackers and distributors of illegal or morally questionable material. |
|
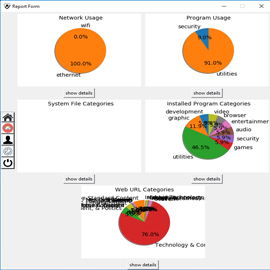 |
Technology is often falsely perceived as the immediate answer to Information Security problems. Information Security is primarily a human factors problem that remains unaddressed. The home computer user is often said to be the weakest link in computer security. Security and privacy threats such as Web cookies and phishing require some form of user complicity or acquiescence. Adequate security does not come with the purchase of the computer but requires additional software, careful settings within applications, appropriate choices of passwords, regular updating of patches, etc. Moreover, as applications are becoming more interesting/ useful and businesses are moving away from paper, home computer users are performing more sensitive tasks online and storing more private data on their computers.
|
|
|
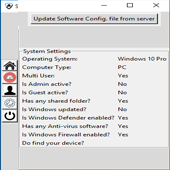 |
| System Setting Form. |
|
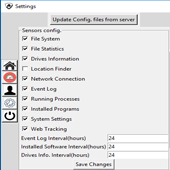 |
| System Comfiguration. |
|
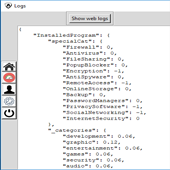 |
| System Log. |
|
|
|
|
| This research tries to record home users’ activities by monitoring their interaction with computer to understand their characteristics, interests and behaviour patterns to predict cybersecurity risks related and provide necessary awareness and alternatives. A User’s activities on a computer describes witch group of user s/he belongs to and what level of security or privacy is required. monitoring individual actions to obtain labelled training data is less costly and more effective in creating a user profile. |
|
University of Rostock
Institute of Computer Science
Farhad Foroughi / Peter Luksch
farhad . foroughi [a] uni-rostock . de
|
|





